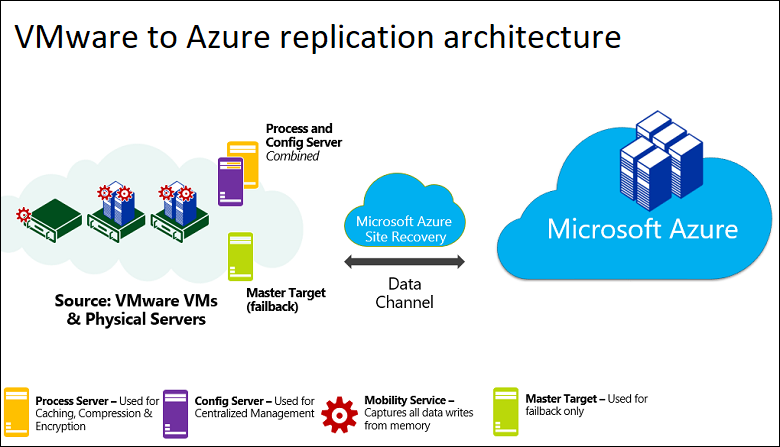
a) Enable audit logon events on AD computer
- Log on to Windows AD DC as a member of the Administrators group.
- Open Administrative Tools, and then click Group Policy Management.
- In the console tree, open Forest: YOUR_FOREST > Domains > YOUR_DOMAIN_NAME, right-click on Default Domain Policy, and then click Edit.
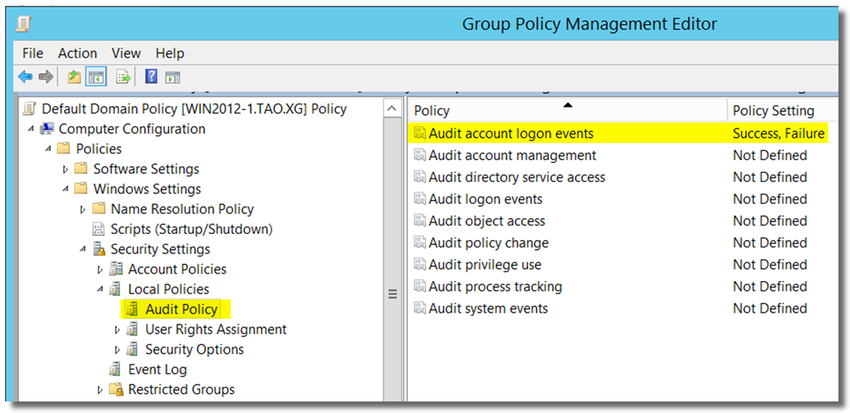
[ Note: You can also edit other group policy as needed. ] - In Group Policy Management Editor, open Computer Configuration > Policies > Windows Settings > Security Settings > Local Policies > Audit Policies.
- Double-click on Audit account logon events, and enable "Define these policy settings: Success and Failure"
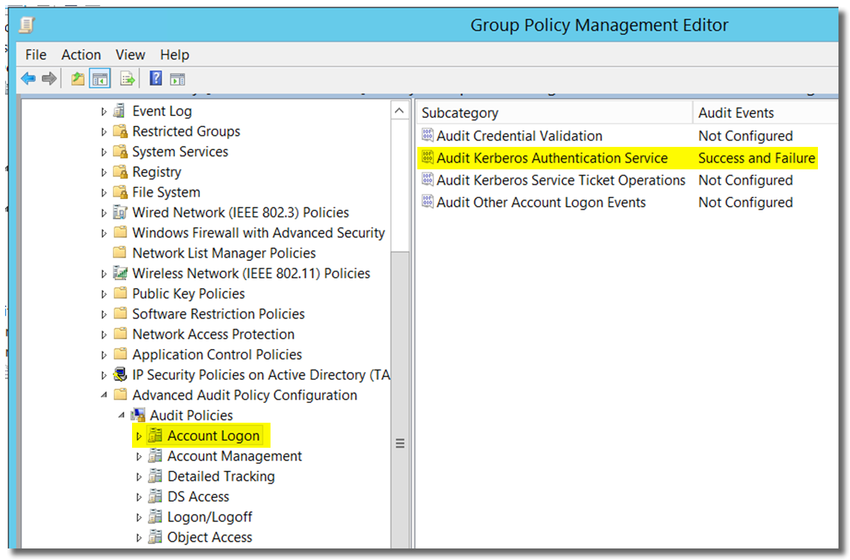
6. Open Computer Configuration > Policies > Windows Settings > Security Settings > Advanced audit policy configuration > Audit Policies > Account Logon
7. Double-click on Audit Kerberos Authentication Service, and enable "Configure the following audit events: Success and Failure"
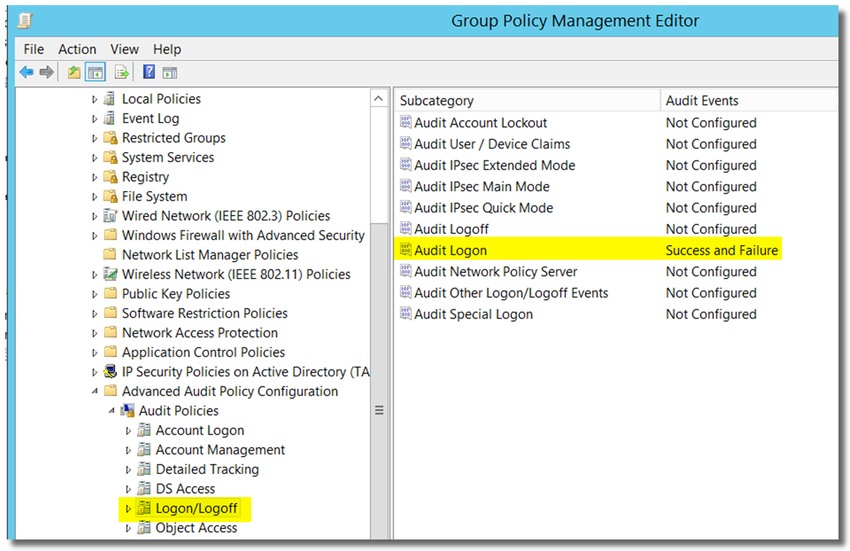
8. open Computer Configuration > Policies > Windows Settings > Security Settings > Advanced audit policy configuration > Audit Policies > Logon/Logof
9. Double-click on Audit Logon, and enable "Configure the following audit events: Success and Failure."
Source : Sophos Firewall: Best practice for STAS - Recommended Reads - Sophos Firewall - Sophos Community